Feature 5 Interactive Maps – Security
Protecting Your Map Data with Access Controls
Nowadays a large amount of geospatial data is available for free and accessible to the general public. Sometimes you can get geospatial data only by accessing different websites, but in other situations you may need to get credentials like login in order to have the possibility to download the desired geospatial data. However, not all the data are available for free and not the entire digital maps available online should be accessible for everyone.
Here at CSV2GEO we are aware about the importance of security when we speak about geospatial data and digital mapping. Since our users are from a wide range of domains, some users might need the highest level of security for the maps created using the “Interactive Maps” tool available at CSV2GEO. Consequently, we have dedicated a feature for the level of security while the user chooses to use the “Interactive Maps” tool in CSV2GEO. This feature can be found under the “Security” menu in the table of attributes, as can be noticed down below. In this “Security” menu the user can observe a list of five bullets: public Map, hidden the URL map, access to provisioned users only map, password protected map and Download markers list. Let’s discover which the differences of these security levels are while the user chooses them during the mapping process here at CSV2GEO.
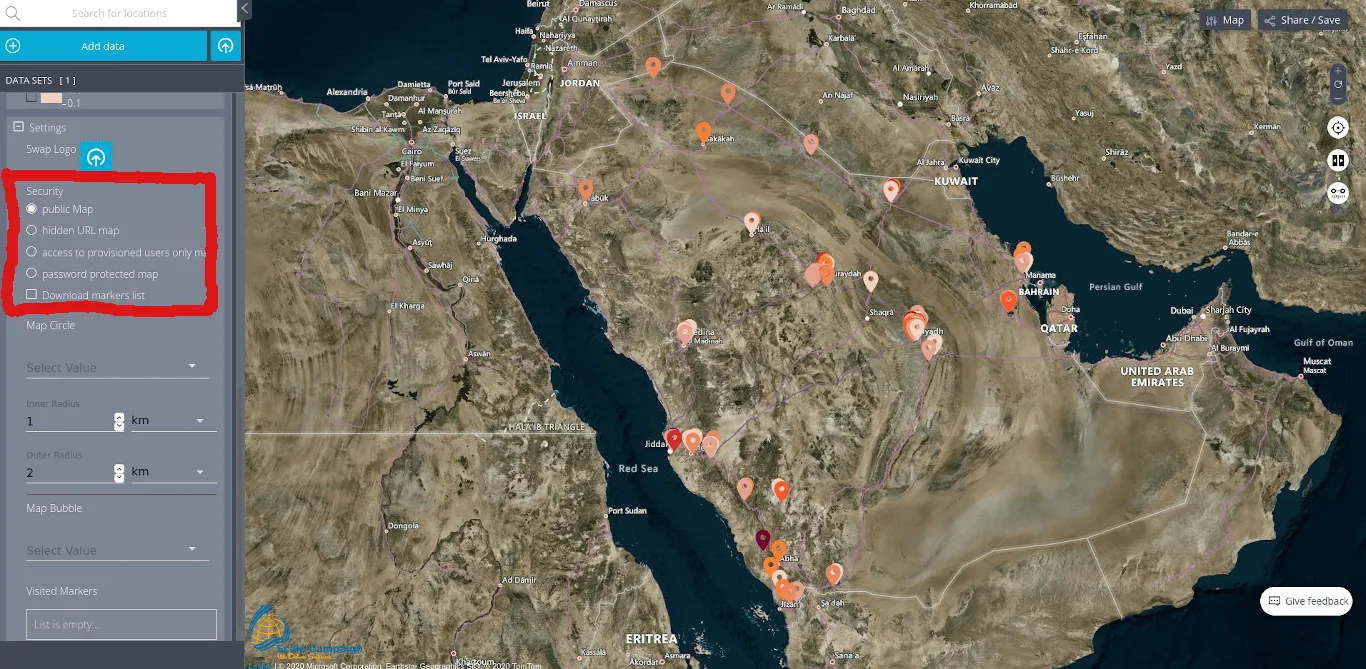
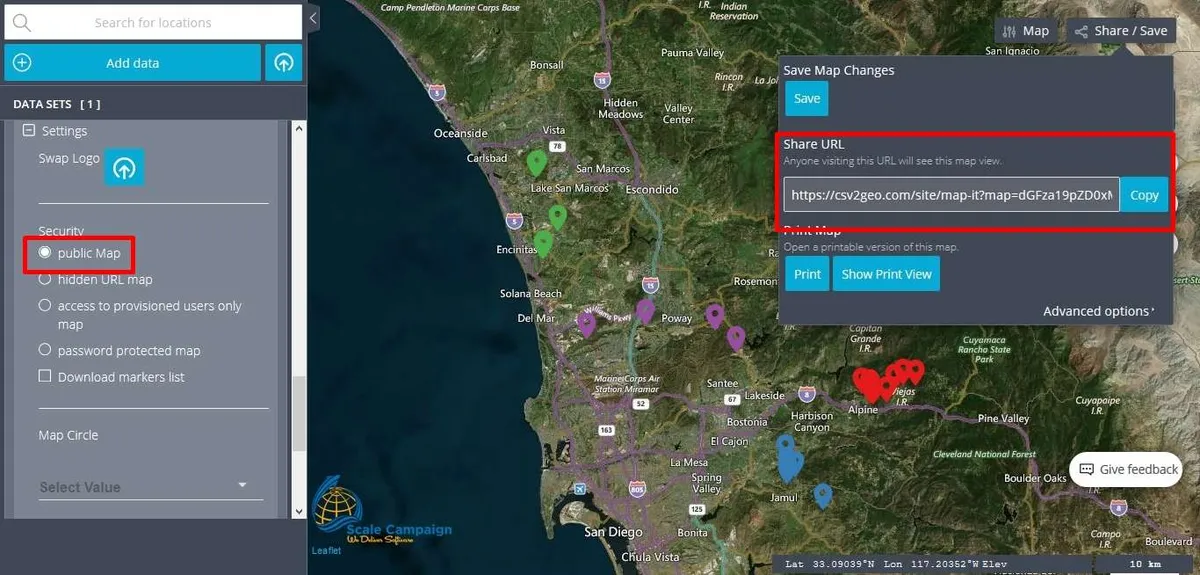
First of all, if the user chooses the level of security called “public Map” than anyone accessing the link of the map can see that map and the information plotted there. In other words, that map is visible for anyone who knows about the link of the map, the link that can be observed in the right part of the map if the user clicks on the “Share/Save” button. This level of security is recommended for those users who want to share their maps via the Internet for different purposes or for those users who are not working with confidential data and they don’t mind if someone else access for their maps.
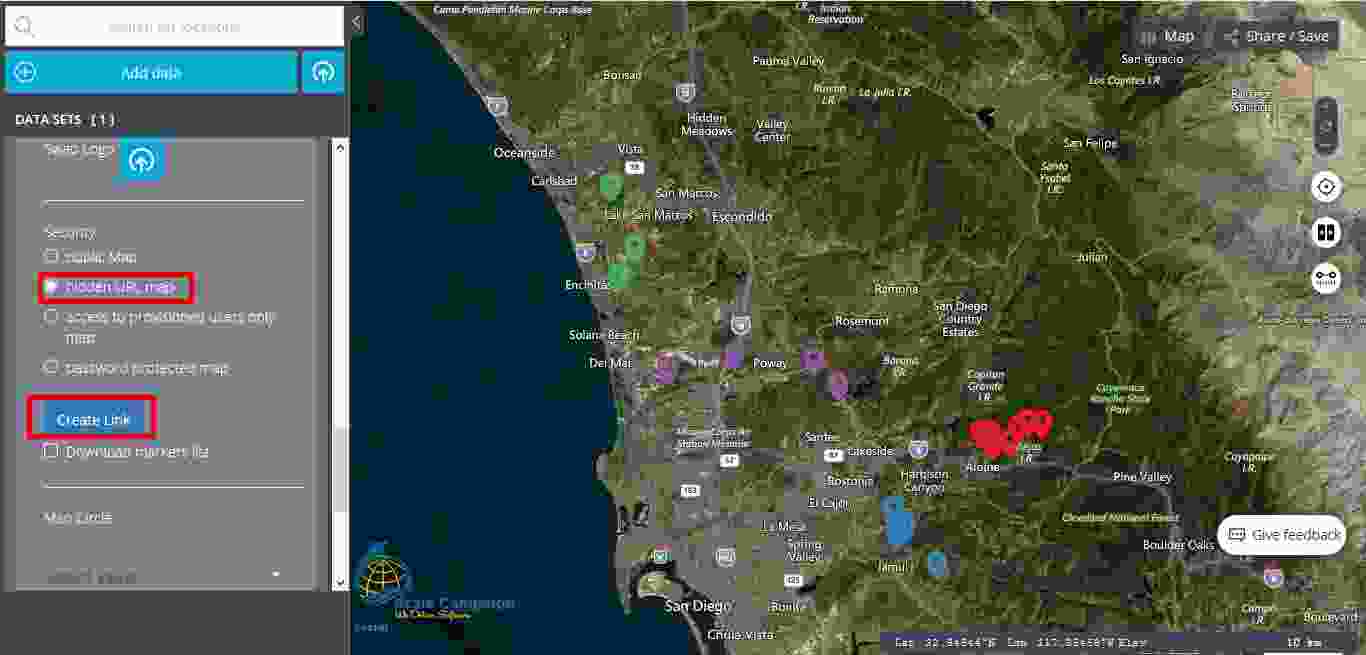
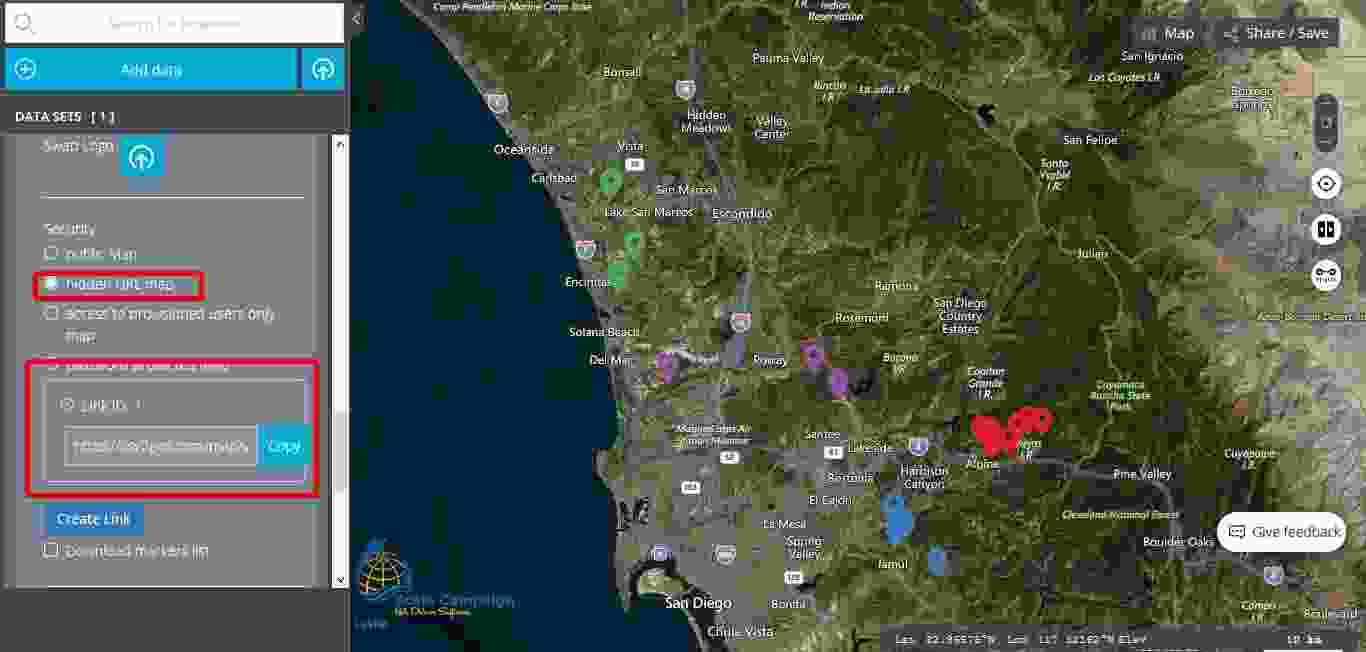
Moving forward to the second level of security, the user will notice “hidden URL map”. This level of security provides to the user the possibility to create a link that will not be public. As soon as the user clicks on the button named “Create Link” a new field opens with a new link that is totally different from the link available in the “Share/Save” section. Consequently, only the user will know the link for this map now and this link will be hidden for the general public. By doing this choice the user improves the level of security for the map created using the “Interactive Maps” tool.
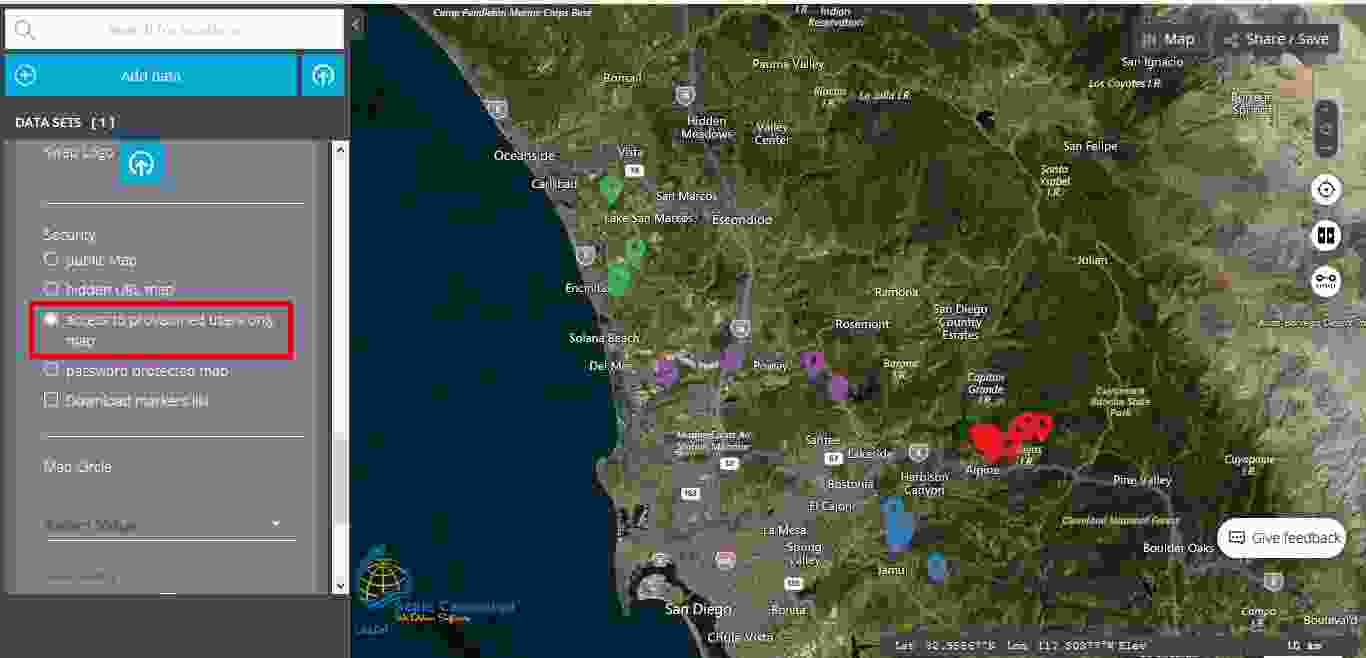
The third level of security is called “access to provisioned users only map”. Actually, this level of security allows only the users of the map to access it. Consequently, if the user works with confidential data, the user can be confident that nobody else will have access to this data.
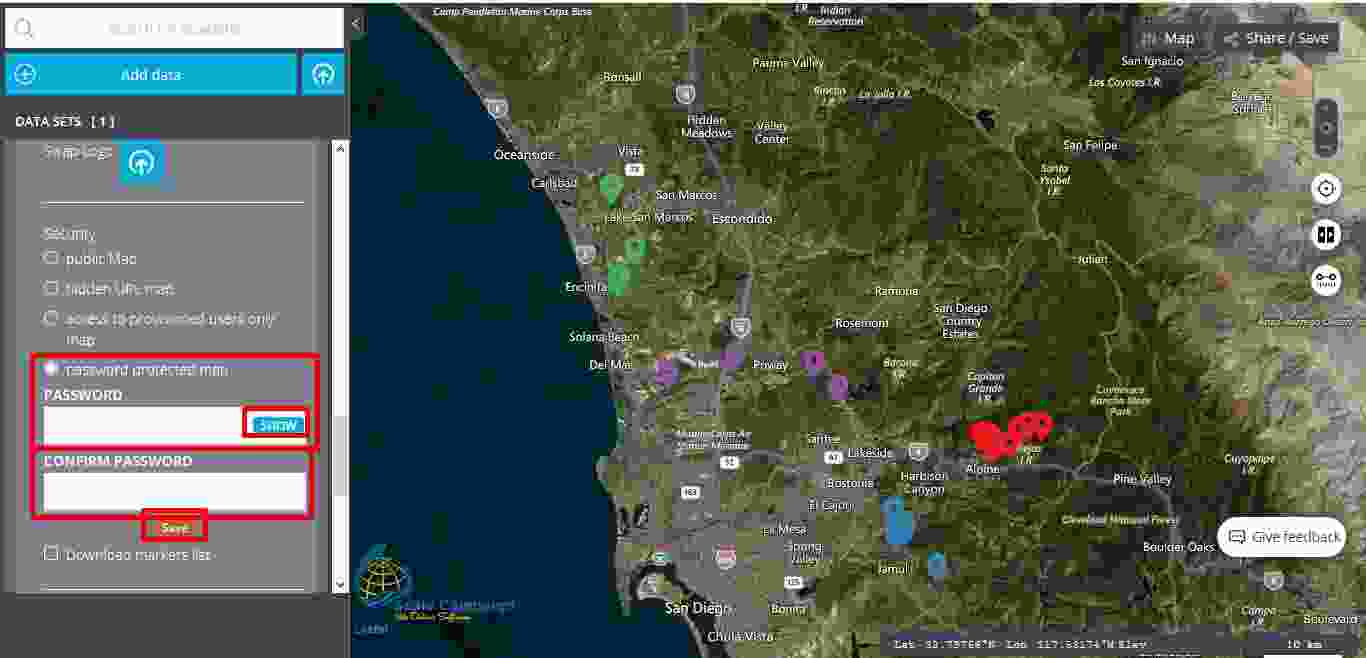
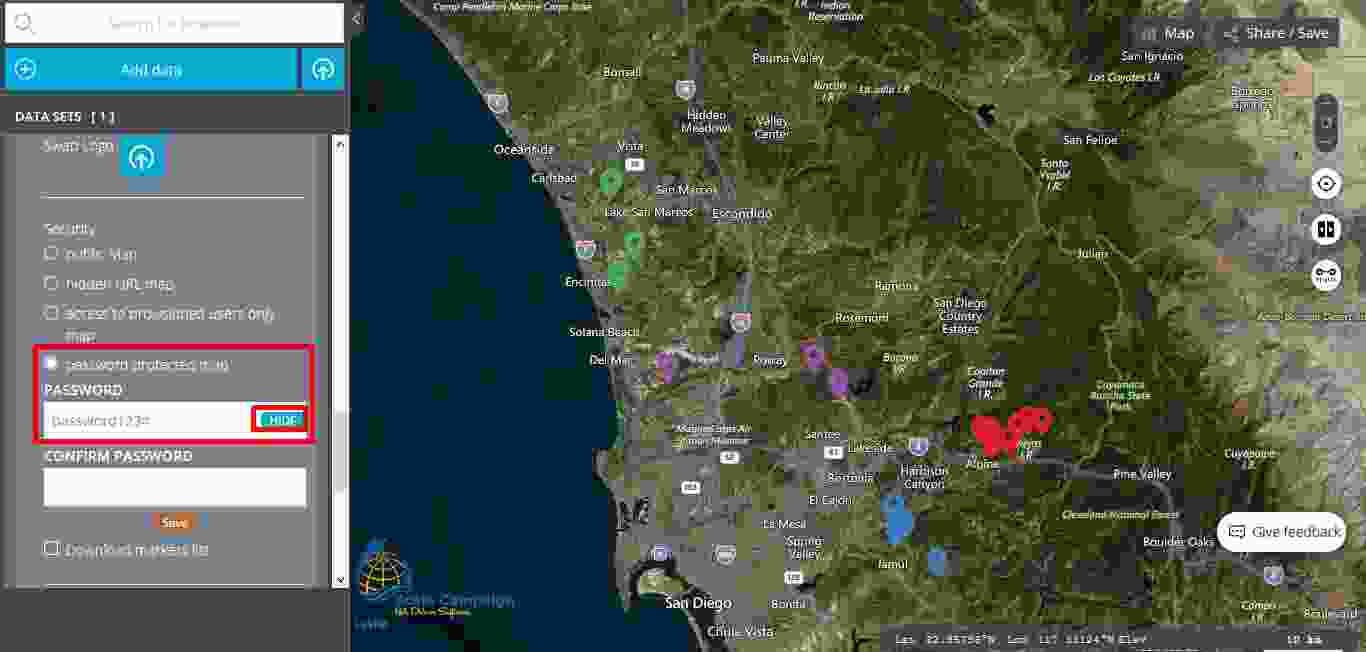
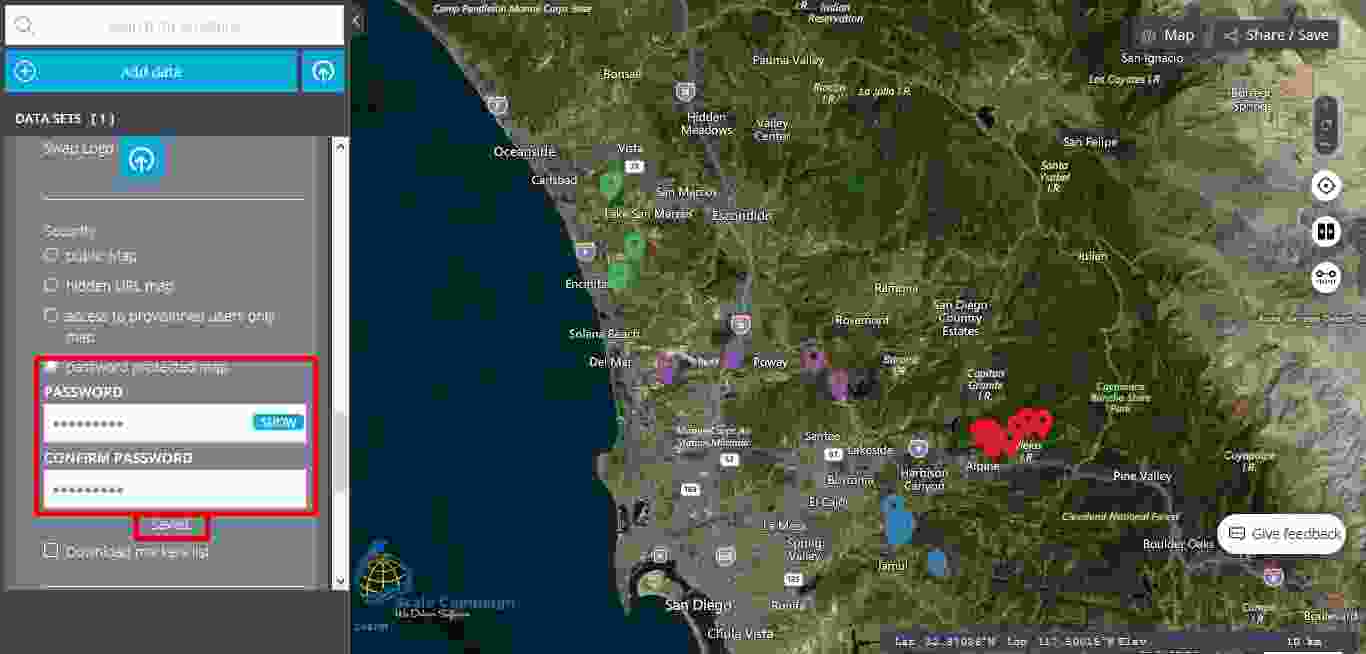
This last level of security, called “password protected map” it is the highest level of security and as its name says, this level protects the map with the help of a password. Consequently, the user should click on the “password protected map” button and then two new fields are opening, namely “Password” and “Confirm password”. Furthermore, the user should fill in both fields and then click on the “Save” button. As soon as under the “Confirm password” field appears “Saved”, then it means that the map is now protected by a password. The user can choose to show or to hide the password during the fill in process.
The last line in the “Security” menu is called “Download markers list” and it doesn’t have the necessary a security role. By checking this feature, the user has the possibility to download the markers list as a table and open it later on in Excel. This feature is very helpful if the user has made updates to the markers. In order to have the possibility to download the markers list as Excel table the user should go to the “Share/Save” button. The user will notice that when the “Download markers list” feature is checked in the “Security” menu, a new button is active. Moreover, by clicking on that button the user will can open or save the markers list as a CSV file and open it later on in Excel as a separate table.
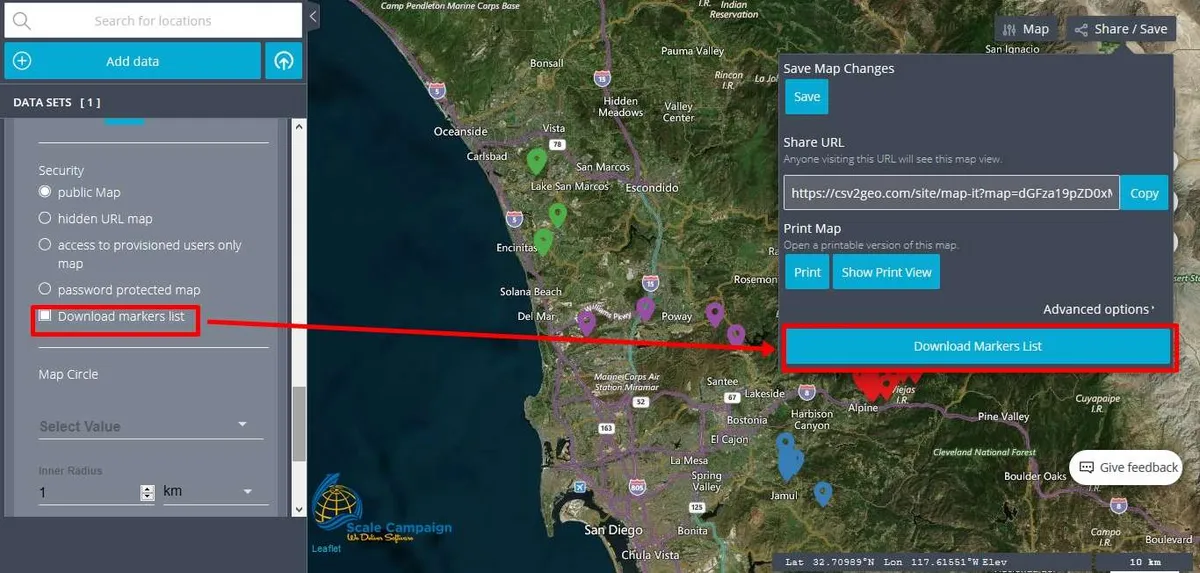
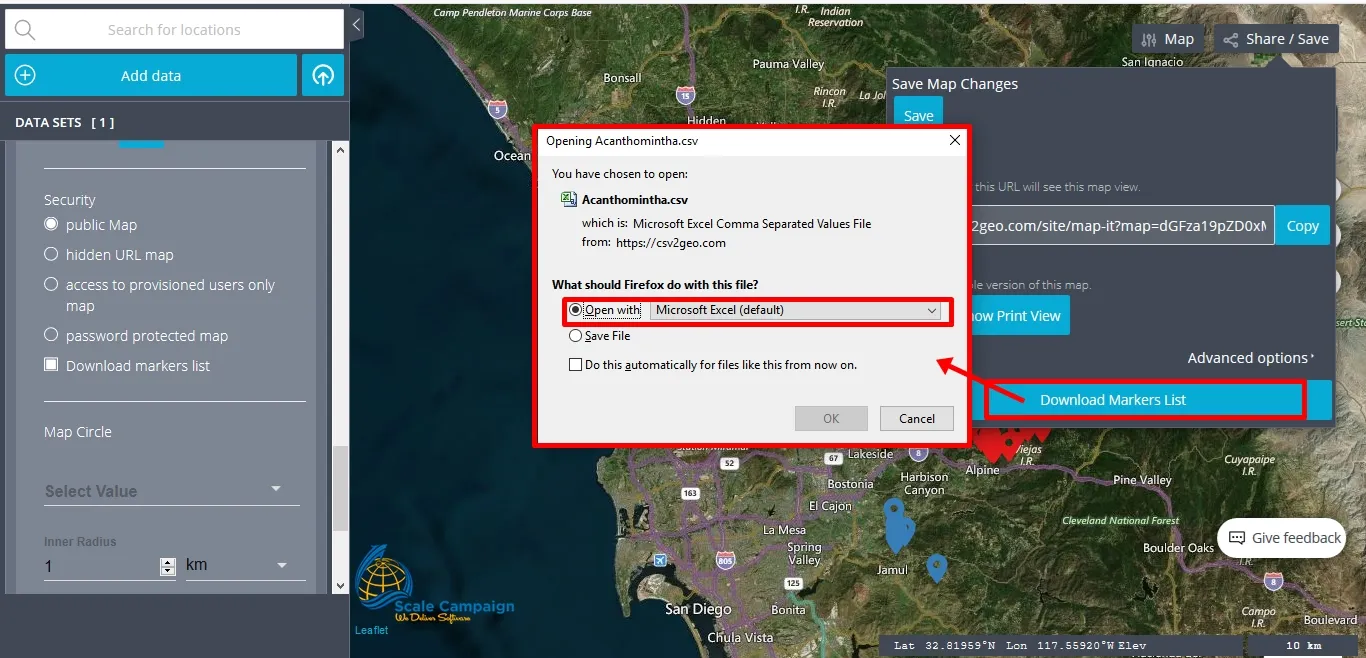
Concluding, we must emphasize that the “Security” menu is very helpful for the users in order to choose exactly the level of security that they might need for their mapping projects. Consequently, when the user chooses to create maps based on geocoded data, the user can choose exactly the desired level of security for the maps created using the “Interactive Maps” tool.